Cyberwarfare and Hacktivism in the Middle East
November 15, 2012 Shem Radzikowski One Comment

Multi-billion dollar Oil & Gas companies are being targeted by a new generation of intelligent and destructive computer viruses that are capable of collecting sensitive information and are capable of destroying entire computer ecosystems.
On August 15, Saudi Aramco, the world’s largest Oil & Gas producer based in Saudi Arabia, admitted that it was targeted by a group of hackers which managed to infect some 30,000 personal computers and possibly stole proprietary information.
Who’s Behind the Attacks
There are mixed reports of whether the group behind the cyber-attack is the Arab Youth Group or the Cutting Sward of Justice, both of which have been linked to regional activist organizations. Reports are still sketchy and although Saudi Aramco CEO, Khalid A. Al-Falih, said that the company reacted quickly to isolate and contain the infection, it is still unclear how much damage was sustained or what data was stolen.
Shamoon, the malware (malicious software) responsible for the attack on the organization, represents what some would call the first widely publicized example of hacktivism. Hacker groups such as Anonymous[1] and LulzSec[2] have typically targeted known Web application vulnerabilities or used distributed-denial-of-service (DDoS) attacks. “This is the first significant use of malware in a hacktivist attack,” said Imperva’s Rob Rachwald, director of security strategy.
Interestingly, instead of staying under the radar and collecting information, the malware was designed to overwrite and wipe the files and the Master-Boot Record of the computers — rendering them useless.
Despite the fact that it is rare to find this type of malware in targeted attacks, Kaspersky Lab suggest that this is the same behavior of the wipe malware found attacking machines in Iran which were infected with another unknown malware that eventually led Kaspersky to discover the Flame virus.
The origin of Shamoon or Flame can’t be verified, but on 16th June 2012 the Washington Post reported that the “United States and Israel jointly developed a sophisticated computer virus nicknamed Flame that collected intelligence in preparation for cyber-sabotage aimed at slowing Iran’s ability to develop a nuclear weapon, according to Western officials with knowledge of the effort.”
Background on Shamoon
The malware infection that crippled the computer systems of Saudi Aramco was dubbed “Shamoon” (Simon in Arabic) after researchers found a reference to a folder by the same name within the malware executable. Although Saudi Aramco stated that the virus did not disrupt any computer systems responsible for oil and gas production, the incident did send a sobering security shock wave throughout the energy sector.
Details of the cyberattack seem to confirm that 75% of the company’s workstations were infected, critical data files deleted and replaced with the image of a burning American flag.
The hackers, who called themselves Cutting Sword of Justice, said that they had released a malicious virus into Saudi Aramco on Aug. 15 that destroyed around 30,000 computers.
To corroborate the hack, the group uploaded onto Pastebin[3] (a website that allows free and anonymous exchange of information) blocks of what they claimed to be the internal IPs (unique addresses) of the infected computers. The attack against the government-owned oil company is said to be in retribution for the Saudi government’s support for “oppressive measures” in the Middle East.
Many analysts believed that the momentum created by the Arab Spring would in some part spill over into Saudi Arabia. Some suggest that the country has one of the most repressive regimes in the Arab world. So much so, that Amnesty International released a report titled “Saudi Arabia: Repression in the Name of Security” in which it revealed that hundreds of people have been arrested for demonstrating, while the government drafted an anti-terror law that would effectively criminalize dissent as a “terrorist crime” and further strip away rights from anyone accused of such offenses.

Saudi Women protesting in the city of Karbala
Recent protests in the country’s eastern province, home to a large Shiite minority and holding 90% of the country’s oil reserves, indicate that despite harsh efforts to quell demonstrations people are still flocking to the streets.
Given the relative hostility of the ruling government, it isn’t at all surprising that the so-called hacktivists (hackers who attack for political reasons rather than profit) have begun branching out into more sophisticated ways of making a statement.
Whether the origin of Shamoon or Flame will ever be identified, isn’t really important. However, evidence suggests that whoever is behind Shamoon, either reverse-engineered some of Flame’s behavior or had direct access to the original source code.
Similar Cyber-attacks
Just two weeks after the Saudi Aramco malware attack, the Doha-based RasGas Company Limited, a joint venture between Qatar Petroleum[4] and ExxonMobil, was hit by a similar virus. A press release of the incident confirmed that “the company’s office computer systems were affected by an unknown virus on Monday, 27th August 2012 Key impact remains in the administrative IT system; Operational Systems on site and offshore are secure. The production and supply of Liquefied Natural Gas (LNG), pipeline gas and associated products are uninterrupted.”
Malware is much more pervasive in the Middle East than in other regions of the globe. The fact that Saudi Aramco go hit by something like Shamoon shouldn’t be a big surprise, particularly given the number of infected systems in the region.
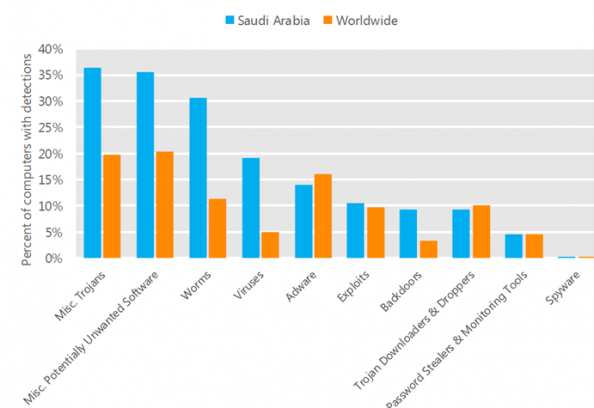
Threat Categories: Worldwide vs Saudi Arabia Source: Microsoft SIR v12
But Saudi Aramco and RasGas weren’t the only organizations to be targeted by hacktivists in the Middle East. In September, the websites of the Arabic news network, Al-Jazeera[5], were hacked by a group sympathetic to the Syrian regime. Al-Jazeera’s English and Arabic websites were affected by the hack, made by a group calling itself al-Rashedon, or “the guided ones”.
“This is a response to your position against the people and government of Syria, especially your support of the armed terrorist groups and spreading false fabricated news,” the group said in a statement blanketing aljazeera.net. “Your website has been hacked, and this is our response to you.”
The Qatari state-owned Al-Jazeera has made a name for itself by covering the region’s instability. But it has also been accused of bias and inconsistency. A number of staff resigned from Al-Jazeera accusing it of being biased towards the Syrian regime but supportive of Bahrain, Qatar’s neighbor.
In September 2011, Wadah Khanfar, a Palestinian widely seen as independent, suddenly left as director-general after eight years in the post and was replaced by a member of the royal family, Sheikh Ahmed bin Jassim al-Thani, a man with no background in journalism.
Almost a year later, on 30 September 2012 the network’s editorial independence was again called into question after its director of news ordered that a speech made by Qatar’s emir to the UN in relation to the debate on Syrian intervention be re-edited despite strong protests by the reporting journalists. Some observers are now suggesting that the once self-proclaimed “independent” Arabic news network is quickly becoming nothing more than an instrument to further Qatar’s foreign policy within the region.
Although the hack on Al-Jazeera was different to those against RasGas and Saudi Aramco, they were all executed with the intention of conveying a politically motivated message.
The sophistication of the malware is increasing to such levels that some experts believe that only groups with considerable resources and expertise would be in a position to create such viruses and that state-run cyberwarfare organizations are behind their development.
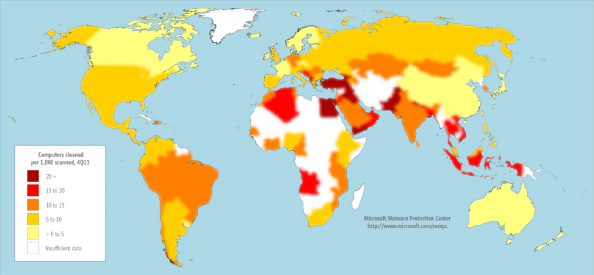
Malware heat map. Source: Microsoft Security Intelligence Report vol. 12
Similarities have been highlighted by Kaspersky Lab and Seculert between Shamoon and Flame, the cyber espionage virus that targeted computers in the Middle East. Shamoon has been noted as unique for having differing behaviour from other malware cyber espionage attacks and is capable of spreading to other computers on the network through exploitation of shared hard drives. Once a system is infected, the virus continues to compile a list of files from specific locations on the system, erase and then send information about these files back to the attacker. Finally, the virus will overwrite the master boot record of the system to prevent it from booting and covering its tracks.
The Usual Suspects: Cyberwarfare
Various groups have come forward claiming responsibility for the attacks but the question still remains: who is responsible for the development of the new generation of malware?
On 1st June 2012, the New York Times reported that “President Obama secretly ordered increasingly sophisticated attacks on the computer systems that run Iran’s main nuclear enrichment facilities, significantly expanding America’s first sustained use of cyberweapons.” The computer security experts who began studying the worm that infected Iran’s nuclear enrichment facilities eventually gave it a name: Stuxnet.
Kaspersky Lab concluded that the sophisticated attack could only have been conducted “with nation-state support.” Proving which nation-state was responsible for Stuxnet will be difficult, but in light of the cyberweapons program which was started under President George W. Bush and then expanded under President Barack Obama, it has been suggested that Israel and the United States may have had direct involvement.
Shortly after Stuxnet’s discovery within Iran’s facilities, security researchers discovered another cyber-espionage worm on computers in Iran, Israel, Sudan, Syria, Lebanon, Saudi Arabia, and Egypt. A researcher from the Budapest University of Technology and Economics said that it
“is certainly the most sophisticated malware we encountered during our practice; arguably, it is the most complex malware ever found.”
Security researchers named the worm “Flame”.
Flame can spread to other systems over a local network (LAN) or via USB stick. It can record audio, screenshots, keyboard activity and network traffic. The program also records Skype conversations and can turn infected computers into Bluetooth beacons which attempt to download contact information from nearby Bluetooth-enabled devices. This data, along with locally stored documents, is sent on to one of several command and control (C&C) servers that are scattered around the world. The program then awaits further instructions from these servers.
Although Flame was discovered in May 2012, computer forensic experts have compiled evidence that suggest Flame may have persisted undetected on infected computers since at least February 2010.
Whether Shamoon, Stuxnet or Flame had state backing or were in some way sanctioned by nation-states will require further research. The irrefutable fact, however, is that this type of malware is being utilized by politically-motivated organizations and demonstrates that the technology is available to anyone with the right connections and an underlying motive to use it.
If organizations are to stand a fighting chance against this new generation of malware, then they need to invest in a cultural change as much as they do in technical safeguards.
[Title photo credit: Lord Jim / Foter / CC BY]
Footnotes
- Anonymous (used as a mass noun) is a loosely associated hacktivist group. It originated in 2003 on the imageboard 4chan, representing the concept of many online and offline community users simultaneously existing as an anarchic, digitized global brain.[4] It is also generally considered to be a blanket term for members of certain Internet subcultures, a way to refer to the actions of people in an environment where their actual identities are not known. ^
- Lulz Security, commonly abbreviated as LulzSec, is a computer hacker group that claimed responsibility for several high profile attacks, including the compromise of user accounts from Sony Pictures in 2011. ^
- A pastebin is a type of web application where it is possible to store text for a certain period of time. This type of website is used by some programmers to store pieces of source code or configuration information, but can also be used by anyone to share any type of text. ^
- Qatar Petroleum (QP) is a state owned petroleum company in Qatar. The company operates all oil and gas activities in Qatar, including exploration, production, refining, transport, and storage. Together, revenues from oil and natural gas amount to 60% of the country’s GDP. Currently it is the third largest oil company in the world by oil and gas reserves. ^
- Al Jazeera, literally “The Island”, is an independent broadcaster owned by the state of Qatar through the Qatar Media Corporation and headquartered in Doha, Qatar. Initially launched as an Arabic news and current affairs satellite TV channel, Al Jazeera has since expanded into a network with several outlets, including the Internet and specialty TV channels in multiple languages. ^
References
Related
Al-Jazeera, Anonymous, Arab Spring, Arab Youth Group, Cutting Sword of Justice, Cyberwarfare, ExxonMobil, Flame, Hacktivism, LulzSec, Malware, Middle East, Oil & Gas, Qatar, Qatar Petroleum, RasGas, Saudi Arabia, Saudi Aramco, Security, Shamoon, Stuxnet Middle East, News, Security, Thoughts
One Comment → “Cyberwarfare and Hacktivism in the Middle East”
Leave a Reply
Subscribe
Subscribe and receive email notifications the moment Dr.Shem publishes a new post.
Our Sponsors
Recent Posts
- My Journey with Ropes: Scaling New Heights
- Climbing Mountains in and Around Pokhara: An Adventure Beyond the Summits
- A Nomad’s Notebook: Charting My Path Across Continents
- From Pierogi to Pavlova: My Transcontinental Childhood
- Riding Through History: A Personal Journey on the Irish Rail System
- Above the Azure: Discovering the Thrills of Paragliding in Malta
- Immersed in Nature: A First-hand Experience of Hiking in Wicklow
- My Emerald Isle: Why Ireland is the Epitome of Home
- Life in Boulder Colorado: A Quick Guide to Boulderites’ Lifestyle, Culture, and Values
- The Spirit of Ireland: A Brief History of Irish Whiskey
- Comparison of Firearm Purchase Procedures in California vs Texas
- First impressions on Austin, Texas and its Tech Scene
- Buying a Gun in California – Not as Easy as it Sounds
- Biometric Hype: A Risky Proposition for Fingerprint and Iris Scanners
- Temple Bar: A Great Place to Live, for the Deaf Insomniacs
- Zero Trust and The Mutating Threat Landscape
- CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
- Mentors: The Priceless Few and Lessons Learned
- Selected by Hackin9 and eForensics Magazines as a Contributing Cybersecurity Expert
- Notes from the Cloud Security Alliance (CSA) Congress EMEA 2015
- Analyzing the Power Consumption of Mobile Antivirus Software on Android Devices
- Poorly Configured Proxies Leaking Information through “X-Forwarded” and “Via” HTTP Request Headers
- CyberSecurity: A Case Study of the Need for Change
- Cyberconfusion: Cyber Security, Cyber-Security or Cybersecurity?
- CyberSecurity: Origins of the Advanced Persistent Threat (APT)
- A Newcomer’s Take on Dublin Town — First Impressions
- Crypto Wars and Messaging: How Secure are Skype and WhatsApp?
- Reduced Cognitive Performance: Open-Plan Offices, Noise and Collaboration
- First Impressions on Working with Huawei’s European Research Center (ERC)
- Lessons I’ve Learnt from various Relationships
- Money and Friends Don’t Always Mix
- X-Pyr 2014: My Annotated Version — An Assistant’s View of the Competition
- Malta Airport Gives Schengen a Slap in the Face
- Officially Selected for the X-Pyr 2014 Competition to Cross the Pyrenees by Paraglider
- A Scuba Diver Never Loses His Stripes
- I’ve Reached Middle Age, or so they say, welcome to the Fabulous Forty (40)
- Dubai Residency Visa: Medical & Blood Tests are a Waste of Time
- Pay-to-Volunteers: A Sad State of Affairs in Africa
- Malaria: Arguably the only African natural resource unwanted by the rest of the world
- Still No Conclusive Evidence Suggesting Syrian Government Used Chemical Weapons
- Will it take one million casualties in Syria before the West gets involved?
- Taking Advantage of Idiosyncrasies and Body Language during Business Meetings and Difficult Situations
- Dubai Holds Great Earning Potential for Anglophone East-Africans
- Absence Makes The Heart Grow Fonder — Does it Really?
- Five Thousand Eight Hundred and Sixty-Two Kilometres from Home
- Avoiding Chronic Short-term Memory Loss on Large Projects
- Invited to Talk about Achieving Enjoyment at Work
- Shove your Hello Tomorrow and give me my Quiet Today
- Professional Certifications: Why get certified in the first place?
- Critique of Media Coverage on BlackBerry’s Share Price Free-fall
This is why we at HID Global are working hard on diverse threat detection solutions that are aimed at identifying and deterring threats from having financial and branding impact.