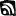CyberSecurity: Origins of the Advanced Persistent Threat (APT)
October 8, 2015 Shem Radzikowski No Comments

For many people within the corporate security community, Google’s January 2010 disclosure that it had been targeted by a sophisticated attack, marked the beginning of the Advanced Persistent Threat (APT) era. Although Google’s disclosure put APT into the spotlight, law enforcement, intelligence and counterintelligence communities had already been using the term for a number of years.
This is the second of a series of articles on CyberSecurity and Advanced Persistent Threats (APTs).
Origins of APT
The term APT was not originally intended to be the generic term that marketers and media have transformed it into. It was developed to refer to specific, known state-sponsored groups in the Asia-Pacific region that conducted attacks against specific targets at the direction of the US government.
The United States Air Force (USAF) coined the phrase Advanced Persistent Threat back in 2006 because teams working within the service needed a way to communicate with counterparts in the unclassified public world. Department of Defense and intelligence community members typically assign classified names to specific threat actors, and use the term intrusion set to describe activities by those threat actors. If the USAF wanted to talk about a certain intrusion set with uncleared personnel, they could not use the classified threat actor name. Therefore, the USAF developed the term APT as an unclassified moniker.[1]
Defining Advanced Persistent Threat
Richard Bejtlich[2], Chief Security Strategist at FireEye, defines APTs as follows:
- Advanced means the adversary can operate in the full spectrum of computer intrusion. They can use the most pedestrian publicly available exploit against a well-known vulnerability, or they can elevate their game to research new vulnerabilities and develop custom exploits, depending on the target’s posture.
- Persistent means the adversary is formally tasked to accomplish a mission. They are not opportunistic intruders. Like an intelligence unit they receive directives and work to satisfy their masters. Persistent does not necessarily mean they need to constantly execute malicious code on victim computers. Rather, they maintain the level of interaction needed to execute their objectives.
- Threat means the adversary is not a piece of mindless code. This point is crucial. Some people throw around the term “threat” with reference to malware. If malware had no human attached to it (someone to control the victim, read the stolen data, etc.), then most malware would be of little worry (as long as it didn’t degrade or deny data). Rather, the adversary here is a threat because it is organized and funded and motivated. Some people speak of multiple “groups” consisting of dedicated “crews” with various missions.
McAfee’s definition for APT is:
Advanced persistent threat (APT) — sophisticated, covert attacks bent on surreptitiously stealing valuable data from targeted and unsuspecting companies — can inflict serious harm to your business. Their relentless, persistent intrusions typically target key users within organizations to gain access to trade secrets, intellectual property, state and military secrets, computer source code, and any other valuable information available.
Evolution of APT
In the early days, attacks typically compromised only a few systems because so few systems were connected to the Internet. But even back then, governments were already targeting other governments using some form of cyber espionage.
One of the earliest publicly documented cases was a first-hand account written by Clifford Stoll’s, The Cuckoo’s Egg, which profiles a West German hacker, Markus Hess, working for the Soviet KGB who, in 1986, broke into a computer at the Lawrence Berkeley National Laboratory (LBNL).[3]
Current APT Landscape
While APTs use many of the same techniques as traditional attacks, they differ from common botnets and malware because they target strategic users to gain undetected access to key assets. APTs can do insidious damage long before an organization knows that it has been hit.
According to Mandiant’s 2015 M-Trends report, the median number of days that threat groups were present on a victim’s network before detection was 205. Although this is 24 days less than the median in 2013, it demonstrates that many organizations don’t have the internal skills nor countermeasures to deal with APTs. What’s worse is that 69% percent of victims learn from a third party that they have been compromised.[4]
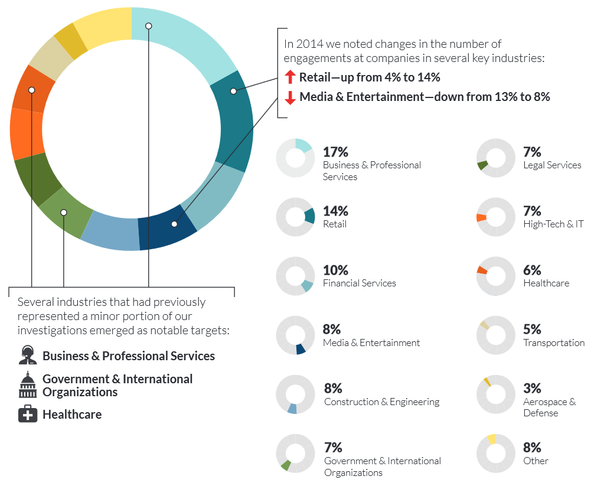
Figure 1: Intrusions by Industry. src: Mandiant
APT Life Cycle
It has been suggested that most sophisticated attackers, regardless of their motives, funding or control, tend to operate in a certain cycle when attacking their targets. Figure 2 shows the evolution of APTs and outlines the APT Life Cycle.
APTs represent a fundamental shift compared to the high-profile hacking events of prior years that commonly targeted networks. Focusing on the weakest links of your defense chain, APTs target specific system vulnerabilities and, more importantly, specific people.
While the victimized organizations vary in size, type, and industry, the individuals they [APTs] target usually fit the same profile: people with the highest-level access to the most valuable assets and resources.[5]
Cybersecurity professionals find themselves struggling to keep up with technical innovation as learning resources for would-be hackers have increased and are often freely available online. The Metasploit framework has revolutionized vulnerability testing, making powerful vulnerability scanners freely available to anyone who calls themselves a penetration tester.
Conclusion
Today’s organizations can’t assume that they will fly under the radar of APTs. As exploits and methods propagate within the hacker community, more organizations will fall victim to targeted attacks and suffer potentially irrecoverable losses.
Advance incident response planning can significantly improve your chances of early detection and more effective remediation.[6] The key to effective APT protection, detection, and response is rigorous implementation of security best practices and ongoing education with your most highly targeted users.
Footnotes
- https://www.academia.edu/6842130/What_APT_Is ^
- http://taosecurity.blogspot.se/2010/01/what-is-apt-and-what-does-it-want.html ^
- The Cuckoo’s Egg: Tracking a Spy Through the Maze of Computer Espionage is a 1989 book written by Clifford Stoll. It is his first-person account of the hunt for a computer hacker who broke into a computer at the Lawrence Berkeley National Laboratory (LBNL).
One day, in August 1986, his supervisor, Dave Cleveland, asked him to resolve a US$0.75 accounting error in the computer usage accounts. He traced the error to an unauthorized user who had apparently used up 9 seconds of computer time and not paid for it, and eventually realized that the unauthorized user was a hacker who had acquired root access to the LBNL system by exploiting a vulnerability in the movemail function of the original GNU Emacs. ^
- M-Trends 2015: A View from the Front Lines, distills the insights gleaned from hundreds of Mandiant incident response investigations in more than 30 industry sectors. The report provides key insights, statistics, and case studies illustrating how the tools and tactics of advanced persistent threat (APT) actors have evolved over the last year. The report also outlines approaches that organizations can take to improve the way they detect, respond to, and contain advanced attacks. ^
- While recent headlines have focused on the most sensational examples of highly organized and wellfunded attacks — Google, Adobe, RSA, Lockheed Martin, SONY, and PBS — thousands of undisclosed attacks have quietly plagued government agencies and corporations large and small worldwide. http://www.mcafee.com/us/resources/white-papers/wp-combat-advanced-persist-threats.pdf ^
- Combating Advanced Persistent Threats – How to prevent, detect, and remediate APTs http://www.mcafee.com/us/resources/white-papers/wp-combat-advanced-persist-threats.pdf ^
Bibliography
Related
Advanced Persistent Threat, APT, APT Life Cycle, Cybersecurity, Google, Hacking, Penetration Testing, Richard Bejtlich, US, USAF Security
Leave a Reply
Subscribe
Subscribe and receive email notifications the moment Dr.Shem publishes a new post.
Our Sponsors
Recent Posts
- Dublin’s Breaking Point: Riots Expose Ireland’s Immigration Crisis
- Ireland’s Immigration Crisis: A Nation Overwhelmed
- My Journey with Ropes: Scaling New Heights
- Climbing Mountains in and Around Pokhara: An Adventure Beyond the Summits
- A Nomad’s Notebook: Charting My Path Across Continents
- From Pierogi to Pavlova: My Transcontinental Childhood
- Riding Through History: A Personal Journey on the Irish Rail System
- Above the Azure: Discovering the Thrills of Paragliding in Malta
- Immersed in Nature: A First-hand Experience of Hiking in Wicklow
- My Emerald Isle: Why Ireland is the Epitome of Home
- Life in Boulder Colorado: A Quick Guide to Boulderites’ Lifestyle, Culture, and Values
- Rekindling a 25-Year-Old Friendship: A Journey Through Time
- The Spirit of Ireland: A Brief History of Irish Whiskey
- Comparison of Firearm Purchase Procedures in California vs Texas
- First impressions on Austin, Texas and its Tech Scene
- Buying a Gun in California – Not as Easy as it Sounds
- Biometric Hype: A Risky Proposition for Fingerprint and Iris Scanners
- Temple Bar: A Great Place to Live, for the Deaf Insomniacs
- Zero Trust and The Mutating Threat Landscape
- CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
- Mentors: The Priceless Few and Lessons Learned
- Selected by Hackin9 and eForensics Magazines as a Contributing Cybersecurity Expert
- Notes from the Cloud Security Alliance (CSA) Congress EMEA 2015
- Analyzing the Power Consumption of Mobile Antivirus Software on Android Devices
- Poorly Configured Proxies Leaking Information through “X-Forwarded” and “Via” HTTP Request Headers
- CyberSecurity: A Case Study of the Need for Change
- Cyberconfusion: Cyber Security, Cyber-Security or Cybersecurity?
- CyberSecurity: Origins of the Advanced Persistent Threat (APT)
- A Newcomer’s Take on Dublin Town — First Impressions
- Crypto Wars and Messaging: How Secure are Skype and WhatsApp?
- Reduced Cognitive Performance: Open-Plan Offices, Noise and Collaboration
- First Impressions on Working with Huawei’s European Research Center (ERC)
- Lessons I’ve Learnt from various Relationships
- Money and Friends Don’t Always Mix
- X-Pyr 2014: My Annotated Version — An Assistant’s View of the Competition
- Malta Airport Gives Schengen a Slap in the Face
- Officially Selected for the X-Pyr 2014 Competition to Cross the Pyrenees by Paraglider
- A Scuba Diver Never Loses His Stripes
- I’ve Reached Middle Age, or so they say, welcome to the Fabulous Forty (40)
- Dubai Residency Visa: Medical & Blood Tests are a Waste of Time
- Pay-to-Volunteers: A Sad State of Affairs in Africa
- Malaria: Arguably the only African natural resource unwanted by the rest of the world
- Still No Conclusive Evidence Suggesting Syrian Government Used Chemical Weapons
- Will it take one million casualties in Syria before the West gets involved?
- Taking Advantage of Idiosyncrasies and Body Language during Business Meetings and Difficult Situations
- Dubai Holds Great Earning Potential for Anglophone East-Africans
- Absence Makes The Heart Grow Fonder — Does it Really?
- Five Thousand Eight Hundred and Sixty-Two Kilometres from Home
- Avoiding Chronic Short-term Memory Loss on Large Projects
- Invited to Talk about Achieving Enjoyment at Work