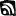Zero Trust and The Mutating Threat Landscape
February 26, 2016 Shem Radzikowski No Comments

Zero Trust (ZT) was heralded as a disruptive network architecture that would finally put an end to internal threats. It was also supposed to bridge the security gap between implicitly trusted internal network zones and untrusted perimeter defences — but did it?
The common view is that there is inadequate visibility, control and protection of user and application traffic transiting high-risk network boundaries, and the assertion that everything on the inside of an organization’s network should be trusted, is rather outdated. Enter Next-Generation Firewalls (NGFW), the devices tasked with addressing these problems and implementing Zero Trust.
Zero Trust, a quick primer
The Zero Trust approach, first proposed by Forrester Research, was intended to address problems by promoting “never trust, always verify” as its guiding principle. With Zero Trust there is no default trust for any entity — including users, devices, applications, and packets — regardless of what it is and its location on or relative to the corporate network.
A Zero Trust network creates micro-perimeters of control and visibility around the enterprise’s most sensitive data assets and the ways in which the enterprise uses its data to achieve its business objectives.[1]
The Zero Trust model eliminates the need to maintain two (or more) separate security zones, a trusted network (usually the internal network) and an untrusted network (external networks). This is an oversimplification, of course, and not every network will so easily be reconfigured. In essence, Zero Trust tries to address internal and external threats by designing networks from the inside out in a modular, scalable way.
It is important to note that Zero Trust isn’t a standard, but rather a conceptual approach to security that’s woven around three main points:[2]
- All resources are securely accessed regardless of location — All traffic is treated as threat traffic until it is verified that the traffic is authorized, inspected, and secured.
- Strict least-privilege access control is mandatory — Properly implement and enforce access control to eliminate human temptation to access restricted resources.
- All network traffic is inspected and logged — To gain network traffic visibility, all traffic is inspected and all activity logged.
These statements can be implemented in any number of ways and still be classed as Zero Trust. Google was said to have implemented Zero Trust within their internal networks by deploying a home-grown solution, the Beyond Corp initiative, which improved on the three base ideas.[3] There is no hard, prescriptive standard to which one must adhere.
The general idea is that by establishing Zero Trust boundaries which compartmentalize different segments of the network, you can protect critical intellectual property from unauthorized applications or users, reduce the exposure of vulnerable systems, and prevent the lateral movement of malware throughout your network. So it goes.
In a study commissioned by Fortinet in May 2015, Forrester was asked to survey 150 IT security decision makers that had implemented next-generation firewalls by asking them, among others, this question: “Once you implemented your NGFW, which of the following product features were actually used?” The results, shown in Figure 1, clearly demonstrate that only a small subset of features were ever utilized.
Where is Zero Trust now?
Despite a number of hardware vendors jumping on the ZT bandwagon, there has been a somewhat lackluster response and sluggish adoption. Marketers have had a great time flaunting NGFW to anyone willing to listen. After all, anything with NG stuck to the beginning is always better than the previous generation, isn’t it?
Figure 2 shows the web search interest in “Zero Trust” as reported by Google Trends. Clearly not a lot of trending going on — the whole ZT arena looks as though it has been sleeping.
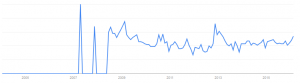
Figure 2: Google Trends of ‘Zero Trust’
In spite of the promising technical aspects of the solutions, I think there are four main reasons why there has been such a lack of interest in Zero Trust and next-gen firewalls, at least when it comes to securing internal networks.
- Firstly, mainstream adoption of virtualization has given organizations plenty to contend with. Physical-to-virtual (P2V) migrations and virtual networking are by no means a trivial task for any organization peppered with legacy systems. And so, the deployment of such micro-perimeter defences has been more of a luxury and less of a priority.
- Secondly, the proliferation of cloud-based technologies, both private and public, has largely made these next-gen devices obsolete before they were given the opportunity to prove themselves in the field. A handful of vendors are still marketing hardware appliances in the hope of a turn around. Honestly, though, without a comparable “virtual appliance” that can be neatly inserted into a software-defined virtual network or sold as a Security-as-a-Service (SECaaS) offering, I don’t think this is a sustainable business model.
- Thirdly, the conglomeration of features in these next-generation firewall devices provide security professionals with a single solution traditionally found across many standalone products. And herein lies the problem. The devices have become too complex and only a few of the included features are ever put into use. According to a Forrester study, most organizations complained of configuration challenges, too much noise and a slowdown in network throughput.
- Lastly, the sheer size of modern cloud providers affords them the economies of scale to deploy cloud-wide, globally-dispersed defences without requiring individual tenants to do the same. Cloud computing has allowed tenants to simplify their network architectures without negatively impacting network security.
Conclusion
The truth of the matter is that neither the approach nor the technologies tasked with improving security have caught on. And while some larger organizations were successful in implementing Zero Trust, a far greater number faced various difficulties when deploying these countermeasures on their physical networks.
Next-generation firewalls that embraced and implemented the Zero Trust model have become bloated, multi-purpose dinosaurs destined for obsolescence — largely due to the universal adoption of cloud computing.
Has Zero Trust missed the boat or will a maturing cloud ecosystem re-inflate interest in the model?
Footnotes
- Forrester created Zero Trust and has worked with numerous clients to design Zero Trust networks. As a result they have developed some best practices to help companies achieve a Zero Trust state more quickly. https://www.forrester.com/fulltext/fulltext/-/E-res120510 ^
- Supporting The Zero Trust Model Of Information Security: The Important Role Of Today’s Intrusion Prevention Systems ^
- Beyond Corp is a broad effort to re-architect the delivery of Google corporate computing services, removing privileges granted solely on the basis of network address. The Overcast architecture blueprint is key to this, presenting a model of machine identity, authentication, and inventory-aware authorization. ^
References
Related
Cloud Computing, Firewall, Forrester, Fortinet, Networking, Next-generation Firewall, NGFW, Palo Alto Networks, Public Cloud, SECaaS, Security, Zero Trust, ZT Security
Leave a Reply
Subscribe
Subscribe and receive email notifications the moment Dr.Shem publishes a new post.
Our Sponsors
Recent Posts
- Dublin’s Breaking Point: Riots Expose Ireland’s Immigration Crisis
- Ireland’s Immigration Crisis: A Nation Overwhelmed
- My Journey with Ropes: Scaling New Heights
- Climbing Mountains in and Around Pokhara: An Adventure Beyond the Summits
- A Nomad’s Notebook: Charting My Path Across Continents
- From Pierogi to Pavlova: My Transcontinental Childhood
- Riding Through History: A Personal Journey on the Irish Rail System
- Above the Azure: Discovering the Thrills of Paragliding in Malta
- Immersed in Nature: A First-hand Experience of Hiking in Wicklow
- My Emerald Isle: Why Ireland is the Epitome of Home
- Life in Boulder Colorado: A Quick Guide to Boulderites’ Lifestyle, Culture, and Values
- Rekindling a 25-Year-Old Friendship: A Journey Through Time
- The Spirit of Ireland: A Brief History of Irish Whiskey
- Comparison of Firearm Purchase Procedures in California vs Texas
- First impressions on Austin, Texas and its Tech Scene
- Buying a Gun in California – Not as Easy as it Sounds
- Biometric Hype: A Risky Proposition for Fingerprint and Iris Scanners
- Temple Bar: A Great Place to Live, for the Deaf Insomniacs
- Zero Trust and The Mutating Threat Landscape
- CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
- Mentors: The Priceless Few and Lessons Learned
- Selected by Hackin9 and eForensics Magazines as a Contributing Cybersecurity Expert
- Notes from the Cloud Security Alliance (CSA) Congress EMEA 2015
- Analyzing the Power Consumption of Mobile Antivirus Software on Android Devices
- Poorly Configured Proxies Leaking Information through “X-Forwarded” and “Via” HTTP Request Headers
- CyberSecurity: A Case Study of the Need for Change
- Cyberconfusion: Cyber Security, Cyber-Security or Cybersecurity?
- CyberSecurity: Origins of the Advanced Persistent Threat (APT)
- A Newcomer’s Take on Dublin Town — First Impressions
- Crypto Wars and Messaging: How Secure are Skype and WhatsApp?
- Reduced Cognitive Performance: Open-Plan Offices, Noise and Collaboration
- First Impressions on Working with Huawei’s European Research Center (ERC)
- Lessons I’ve Learnt from various Relationships
- Money and Friends Don’t Always Mix
- X-Pyr 2014: My Annotated Version — An Assistant’s View of the Competition
- Malta Airport Gives Schengen a Slap in the Face
- Officially Selected for the X-Pyr 2014 Competition to Cross the Pyrenees by Paraglider
- A Scuba Diver Never Loses His Stripes
- I’ve Reached Middle Age, or so they say, welcome to the Fabulous Forty (40)
- Dubai Residency Visa: Medical & Blood Tests are a Waste of Time
- Pay-to-Volunteers: A Sad State of Affairs in Africa
- Malaria: Arguably the only African natural resource unwanted by the rest of the world
- Still No Conclusive Evidence Suggesting Syrian Government Used Chemical Weapons
- Will it take one million casualties in Syria before the West gets involved?
- Taking Advantage of Idiosyncrasies and Body Language during Business Meetings and Difficult Situations
- Dubai Holds Great Earning Potential for Anglophone East-Africans
- Absence Makes The Heart Grow Fonder — Does it Really?
- Five Thousand Eight Hundred and Sixty-Two Kilometres from Home
- Avoiding Chronic Short-term Memory Loss on Large Projects
- Invited to Talk about Achieving Enjoyment at Work