From Internet Censorship to Real-time Content Manipulation
April 28, 2012 Shem Radzikowski 3 Comments

For those of us who live in the Middle East, Internet censorship and partial access to services is a daily reality. The UAE’s two primary Internet Service Providers (ISPs), Du & Etisalat, actively monitor and filter access to Internet sites and content that the government deems inappropriate.
But censorship of the Internet is only part of what I wanted to discuss here. I’m more interested in new technological advances that are helping these repressive governments achieve new levels of control and surveillance.
Who are the Enemies of the Internet
Reporters without Borders (Reporters sans Frontières, RSF), a Paris-based international non-governmental organization that advocates freedom of the press, has just released their annual Internet Enemies Report which reveals some surprising findings.
Internet content filtering is growing but Internet surveillance is growing even more. Censors prefer to monitor dissidents’ online activities and contacts rather than try to prevent them from going online.
–RSF
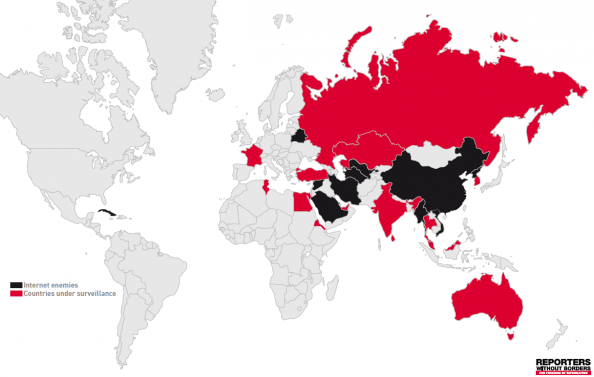
Enemies of the Internet
According to the report, twelve countries fall under the Enemies of the Internet category and are classified as such if they demonstrate a capacity to censor news and information online, but also for their almost systematic repression of Internet users: Bahrain, Belarus, Burma, China (excluding Hong Kong and Macau), Cuba, Iran, North Korea, Saudi Arabia, Syria, Turkmenistan, Uzbekistan, Vietnam.
Countries under Surveillance
The fourteen countries listed under the Countries under Surveillance category are those that actively monitor, report and/or have in place frameworks that encourage ISPs to report on their subscribers’ Internet activities: Australia, Egypt, Eritrea, France, India, Kazakhstan, Malaysia, Russia, South Korea, Sri Lanka, Thailand, Tunisia, Turkey, United Arab Emirates.
It’s quite shocking to see two Western countries, Australia and France, make this list.
Australia, whose government clings to a dangerous content filtering system, has persuaded ISPs to create a voluntary system of information disclosure. It has also formed a News Media Council which “could turn out to be dangerous for freedom of information in the blogosphere.” France is on the list because it continues its “three-strikes” policy on illegal downloading and allows for official filtering of the Web.
Western Technology for Repressive Regimes
Some of the world’s most repressive regimes are (ab)using technologies developed, and in most cases sold to them, by Western corporations.
To enhance their surveillance abilities, repressive regimes turn to specialized companies for ever more effective equipment and software for filtering, monitoring and Deep Packet Inspection.
— RSF, Internet Enemies Report 2012
The report names the US company Blue Coat, for its activities in Syria, Vodafone and Etisalat, for “criminal liability in participation in the harming and killing of demonstrators by cutting off the Internet and telecommunication services in Egypt arbitrarily“, Amesys, a French company which supplied Col. Gaddafi, and Area S.p.A. [1], an Italian company for its cooperation with the Assad regime (Reporters sans Frontiers, 2012).
In addition to the existing censorship policies in the UAE, according to Major Salem Obaid Salmeen, Dubai’s deputy director of anti-electronic crimes, social networking sites like Twitter and Facebook are subject to round-the-clock monitoring by dedicated teams in Dubai and other emirates.[2] Many more companies are implicated by similar reports (Sadafy, 2012).
McAfee and its SmartFilter technology was mentioned in relation to filtering content in Saudi Arabia, UAE, Kuwait, Bahrain, Oman and Tunisia in a bulletin released by the OpenNet Initiative[3] (Noman & York, 2011).
Western-built automated filtering solutions to block mass content, such as websites that provide sceptical views of Islam, secular and atheist discourse, sex, GLBT, dating services, and proxy and anonymity tools. These lists of sites are maintained by the Western company vendors. The ISPs also use these tools to add their own selected URLs to the companies’ black lists.
— OpenNet Initiative
Out of all these companies, only Websense has gone on record “opposing the use of its software for the purposes of government censorship, except for the protection of minors from pornography.” This technology is actively being used to hamper and at times completely stop people’s ability to create and share vital content during times of crisis.
Are we advocating the use of Western products to oppress the people of sovereign countries and deny them basic human rights? It seems that the West’s motivation has shifted from government & resource-based interference (oil, gas, minerals) to that of controlling the greater population. Look at what happened during the Arab Spring.[4]
The Next Wave of Technological Warfare
We can only estimate the total number of blogs, somewhere around 100 million, according to Pingdom. The task of censoring, classifying and updating the classification databases is quite the task with many legitimate sites being wrongly classified and subsequently blocked.
But if you thought that the situation was bad enough as it is, then prepare yourselves for a new wave of technological warfare that will make the current systems look like stone-age tools.
You see, the problem right now is that the end user is fully aware that a site has been blocked. They receive any number of messages telling them that a site is blocked and why.
Utopian Censorship
Imagine a world where censorship was transparent and completely hidden from the consumer. Where the browsing experience is no longer interrupted by intrusive “restricted” messages, but instead, the page renders properly and fills with content. The people read and consume that which is presented without ever questioning its authenticity.
The next wave will consist of governments and corporations being able to render a fully readable page without alerting anyone to what is really happening behind the scenes. This is the ultimate deception. Not only will an oppressive government have the ability to rewrite the content as they see fit, the audience will never (or very rarely) know the true content, nor the publisher be aware of the ongoing deception.
Consider a simple scenario of browsing to the New York Times website, but instead of a page which should read “19 Killed in State-Sanctioned Assassination” the content is manipulated to read “29 Government Soldiers Wounded in Rebel Skirmish” — not only changing the slant but also replacing words and statistics of importance.
Technology such as this would singlehandedly change the way people interact with one another and transform the Internet into the most powerful propaganda and manipulation tool in existence.
Real-time Content Manipulation
When a people are aware of manipulation and censorship, they are likely to seek alternative and trustworthy sources of information. With current tools, the regime might be able to stop the access but they won’t be able to satisfy the underlying thirst for knowledge.
But what if whole sentences, paragraphs and ideas could be automatically and effortlessly redacted down to whatever the regime wants — real-time content manipulation and thought control.
And if you think that technology like this doesn’t yet exist, consider Narrative Science, a company that trains computers to write news stories. The generated articles are already running on the websites of respected publishers like Forbes, as well as other Internet media powers (many of which are keeping their identities private) (Levy, 2012).
The fact that customers wish to remain anonymous is, in my mind, a clear indication that the spread of the technology is far greater than what is being reported and that the wave is already upon us.
Automated Insights, a company based out of North Carolina, is also a major player in this new content game, much like Narrative Science, their website blurb reads: “Our technology platform automatically transforms raw data into compelling narrative content (articles, summaries, headlines), visual displays (charts, tables, graphs) and interactive applications (mobile and Twitter/Facebook-based social applications).:
At the moment, Narrative Science admits to only looking at sporting events and financial markets, however, it is predicted that the technology will be available to write whole news stories within 15 years and that 90% of all news will be written in this way (Levy, 2012).
Eventually, the algorithms will be refined to such a degree that the content and the news will be reorganized, redacted, censored and rewritten as it moves dynamically from one Internet gateway to the next. Implementing such algorithms in existing systems would be a trivial task.
The right to communicate cannot be ignored … The internet is the most powerful potential source of enlightenment ever created.
— Dr Hamadoun Toure [5]
How long before this type of manipulative technology becomes abused by democratic and so-called “free” countries to serve their own propaganda agendas?
[Title photo credit: Eric Drooker]
Footnotes
- Area S.p.A. finally pulled out of Syria after an international campaign criticizing its cooperation with the Assad regime. ^
- The security services no longer interrogate and torture a prisoner for the names of his accomplices. Now they want his Facebook, Skype and Vkontakte passwords. It is the same in Bahrain, Turkmenistan or Syria. ^
- The OpenNet Initiative is a collaborative partnership of three institutions: the Citizen Lab at the Munk School of Global Affairs, University of Toronto; the Berkman Center for Internet & Society at Harvard University; and the SecDev Group (Ottawa). ^
- Arab Spring is a revolutionary wave of demonstrations and protests occurring in the Arab world that began on Friday, 17 December 2010. ^
- Dr Hamadoun Toure is the secretary-general of the International Telecommunication Union (ITU) and was interviewed as part of a BBC survey of more than 27,000 adults across 26 countries. ^
References
Related
Arab Spring, Censorship, Government, Internet Censorship, Journalism, Manipulation, Middle East, Reporters without Borders, RSF, Surveillance, UAE Middle East, News, Security, Thoughts
3 Comments → “From Internet Censorship to Real-time Content Manipulation”
Trackbacks For This Post
-
CISPA & CCDP: Digital Snooping Laws to Rule them All | Dr.Shem -
11 years ago
[…] already touched on Reporters sans Frontières’s recently released Internet Enemies Report in which they discussed countries with poor records of privacy protection or even outright […]
Leave a Reply
Subscribe
Subscribe and receive email notifications the moment Dr.Shem publishes a new post.
Our Sponsors
Recent Posts
- My Journey with Ropes: Scaling New Heights
- Climbing Mountains in and Around Pokhara: An Adventure Beyond the Summits
- A Nomad’s Notebook: Charting My Path Across Continents
- From Pierogi to Pavlova: My Transcontinental Childhood
- Riding Through History: A Personal Journey on the Irish Rail System
- Above the Azure: Discovering the Thrills of Paragliding in Malta
- Immersed in Nature: A First-hand Experience of Hiking in Wicklow
- My Emerald Isle: Why Ireland is the Epitome of Home
- Life in Boulder Colorado: A Quick Guide to Boulderites’ Lifestyle, Culture, and Values
- The Spirit of Ireland: A Brief History of Irish Whiskey
- Comparison of Firearm Purchase Procedures in California vs Texas
- First impressions on Austin, Texas and its Tech Scene
- Buying a Gun in California – Not as Easy as it Sounds
- Biometric Hype: A Risky Proposition for Fingerprint and Iris Scanners
- Temple Bar: A Great Place to Live, for the Deaf Insomniacs
- Zero Trust and The Mutating Threat Landscape
- CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
- Mentors: The Priceless Few and Lessons Learned
- Selected by Hackin9 and eForensics Magazines as a Contributing Cybersecurity Expert
- Notes from the Cloud Security Alliance (CSA) Congress EMEA 2015
- Analyzing the Power Consumption of Mobile Antivirus Software on Android Devices
- Poorly Configured Proxies Leaking Information through “X-Forwarded” and “Via” HTTP Request Headers
- CyberSecurity: A Case Study of the Need for Change
- Cyberconfusion: Cyber Security, Cyber-Security or Cybersecurity?
- CyberSecurity: Origins of the Advanced Persistent Threat (APT)
- A Newcomer’s Take on Dublin Town — First Impressions
- Crypto Wars and Messaging: How Secure are Skype and WhatsApp?
- Reduced Cognitive Performance: Open-Plan Offices, Noise and Collaboration
- First Impressions on Working with Huawei’s European Research Center (ERC)
- Lessons I’ve Learnt from various Relationships
- Money and Friends Don’t Always Mix
- X-Pyr 2014: My Annotated Version — An Assistant’s View of the Competition
- Malta Airport Gives Schengen a Slap in the Face
- Officially Selected for the X-Pyr 2014 Competition to Cross the Pyrenees by Paraglider
- A Scuba Diver Never Loses His Stripes
- I’ve Reached Middle Age, or so they say, welcome to the Fabulous Forty (40)
- Dubai Residency Visa: Medical & Blood Tests are a Waste of Time
- Pay-to-Volunteers: A Sad State of Affairs in Africa
- Malaria: Arguably the only African natural resource unwanted by the rest of the world
- Still No Conclusive Evidence Suggesting Syrian Government Used Chemical Weapons
- Will it take one million casualties in Syria before the West gets involved?
- Taking Advantage of Idiosyncrasies and Body Language during Business Meetings and Difficult Situations
- Dubai Holds Great Earning Potential for Anglophone East-Africans
- Absence Makes The Heart Grow Fonder — Does it Really?
- Five Thousand Eight Hundred and Sixty-Two Kilometres from Home
- Avoiding Chronic Short-term Memory Loss on Large Projects
- Invited to Talk about Achieving Enjoyment at Work
- Shove your Hello Tomorrow and give me my Quiet Today
- Professional Certifications: Why get certified in the first place?
- Critique of Media Coverage on BlackBerry’s Share Price Free-fall

eventually also .. youngsters will find ways to break the loop even write counter algorithms. it is really REALLY hard to maintain oppression.
I hope you’re right. If it were ever to happen, I hope that the introduction of such manipulation algorithms would have some backdoor to thwart them even if installed at the ISP or country level.