CyberSecurity: A Case Study of the Need for Change
October 15, 2015 Shem Radzikowski One Comment

It’s not every day that you get to play the role of the chief information officer (CIO) of a Fortune 100 company. However, in light of recent high-profile cybersecurity breaches, let’s imagine for a moment that you are a CIO who is busy preparing to deliver a rather sobering cybersecurity briefing.
This is the first of a series of articles that I’ll be posting on CyberSecurity and Advanced Persistent Threats (APTs).
Much of what will be covered has been obtained from numerous sources — publications, whitepapers, conferences, blogs, personal experience and interviews — in the hope of presenting actionable guidance within a contemporary setting.
CyberSecurity Incident Briefing
Being the bearer of bad news is never easy, particularly so when the news is likely to derail a multi-billion dollar corporation. And so, having completed the postmortem on a sophisticated hack that ran circles around your cyberdefences, you have been called in front of the chief executive officer (CEO) and the board of directors to deliver your briefing.
You take a moment to compose your thoughts and then begin to speak:
It took the attackers only six minutes to circumvent the perimeter defenses. From there, they achieved domain administrator privileges in less than 12 hours. In less than a week they fully compromised all 30 of our global domains. They harvested more than 200,000 credentials, giving them the ability to log in to the network masquerading as any of us, they could even change our investment elections in our 401(k)s or transfer money out.
There was no place on our global network they could not go and only a handful of computers they did not have easy access to, only 10 percent of our manufacturing facilities are behind firewalls, segregating them from our network. The attackers were in a position to electronically transfer millions of dollars out of our bank accounts through our accounts payable system. Their tools did not set off any alarms, our antivirus software did not trigger any alerts.
They had direct access to our manufacturing environment and could affect both the quality of our production processes and safety on our shop floors. They had access to our most sensitive intellectual property, including our past, current and future plans for major acquisitions and divestitures as well as the results of the billions of dollars we have invested in a decade of research and development.
And, in the end, they were able to steal all the data. We were not able to stop them, or even see them in our network.
While helpless panic filled the boardroom, it also marked a dramatic shift in the way the organization viewed cybersecurity. This watershed moment granted a previously neglected aspect of operational security the mandate to rethink its mitigation strategy.
The Need for Change
The above example was a case of too little, too late. And although the damage here had been done, many of the board members held non-executive positions at other Fortune 100 companies. Their minds were busy assessing the likelihood of similar cybersecurity failures at these other organizations.
The questions they were asking: “What if someone does this to us again? How would we fare? How are we positioned to make an attacker’s tasks difficult, to detect that an attack scenario is underway, and to respond to attacks we detect?[1]
The ten assessment scenarios shown in Figure 1 were developed by Ernst & Young’s attack and penetration teams based on their previous encounters with advanced persistent threats (APTs).
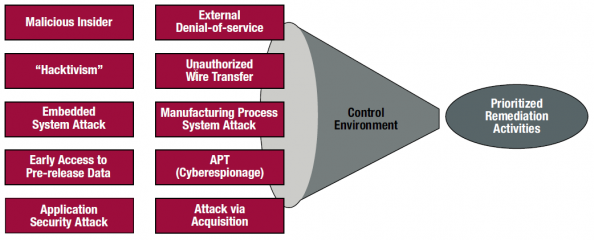
Figure 1: Ten Assessment Scenarios
These ten scenarios, although not an exhaustive list, can serve as a good starting point for organizations trying to come to terms with an adversary whose differing motives and increasingly sophisticated attacks pose significant risk to their operations.
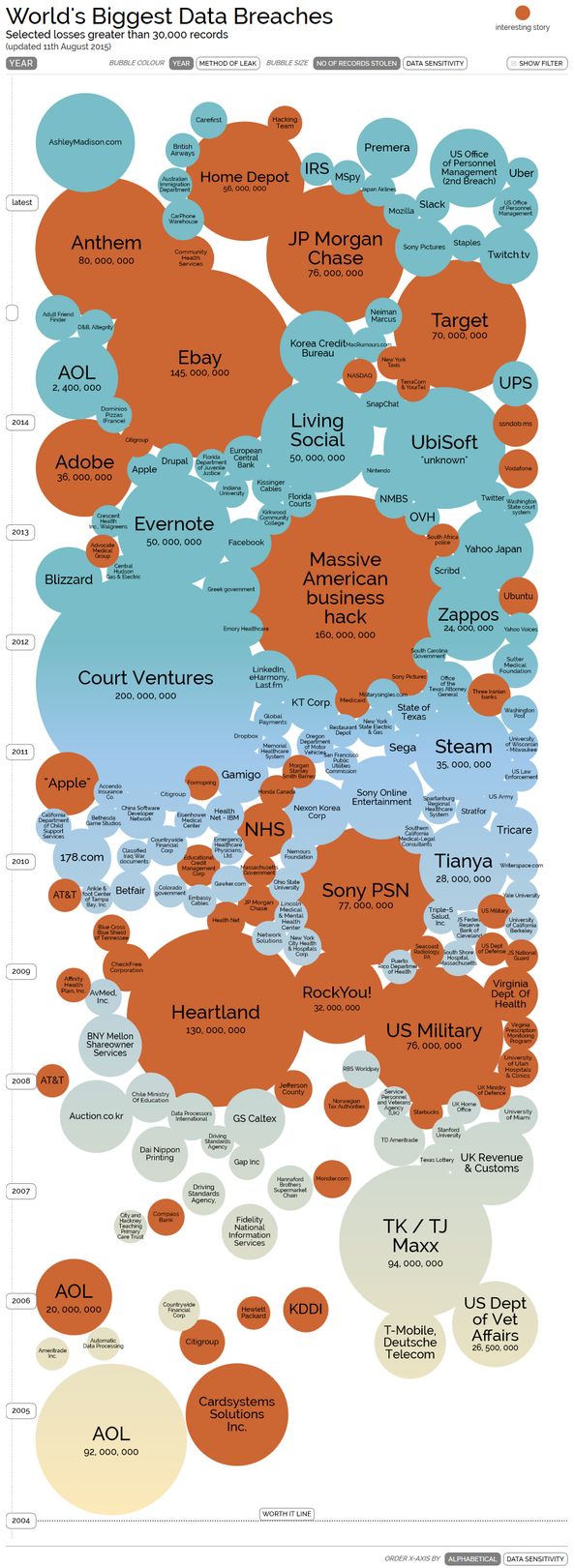
Visualizing the Biggest Data Breaches
Only a very small proportion of attacks receive national or international media attention. The vast majority of organizations, unless required by law, will try to minimize the negative press and never fully disclose the scale of a hack. After all, would you trust a bank to look after your money when they struggle to secure their own corporate website?
The scale of the problem can be seen in the Figure 2, and even these have been filtered to show breaches where total losses amounted to at least 30,000 records per incident. For a fully interactive and up to date version of the data visit the source.
Conclusion
The incident briefing, as described by our CIO to the CEO and the board, reflected an urgent need to fundamentally shift how the enterprise approached cybersecurity. This need was driven primarily by one key fact: The threats that enterprises face by being connected to the Internet are evolving at a much faster pace than the information security architectures, technologies and processes they have deployed to thwart them.[2]
The threats that enterprises face by being connected to the Internet are evolving at a much faster pace than the information security architectures, technologies and processes they have deployed to thwart them.
While following prescriptive guidance will dramatically improve an organization’s preparedness in thwarting attacks, it is worth noting that guidance alone is no silver bullet. Transforming the security posture will only be helpful if such transformation is performed on a a continual basis.
Advanced Persistent Threats are actively engaged in reshaping their attack philosophies. If organizations are to mitigate such efforts, they need to be equally nimble at embracing novel approaches to cybersecurity.
Footnotes
- The Ernst & Young (EY) engagement encompassed the design of a broad series of assessments not intended to measure compliance with policy or conformance to leading practice/technology controls, but rather to focus on assessing the company’s cybersecurity posture in the face of attacks other Fortune 100 companies had recently suffered. ^
- ISACA has designed and created Responding to Targeted Cyberattacks primarily as an educational resource for security, governance and assurance professionals. ^
Bibliography
Related
Advanced Persistent Threat, APT, Attack, CIO, Cyber Security, Cybersecurity, Data Breach, Ernst & Young, EY, Fortune 100, Hack, Penetration Security, Thoughts
One Comment → “CyberSecurity: A Case Study of the Need for Change”
Leave a Reply
Subscribe
Subscribe and receive email notifications the moment Dr.Shem publishes a new post.
Our Sponsors
Recent Posts
- My Journey with Ropes: Scaling New Heights
- Climbing Mountains in and Around Pokhara: An Adventure Beyond the Summits
- A Nomad’s Notebook: Charting My Path Across Continents
- From Pierogi to Pavlova: My Transcontinental Childhood
- Riding Through History: A Personal Journey on the Irish Rail System
- Above the Azure: Discovering the Thrills of Paragliding in Malta
- Immersed in Nature: A First-hand Experience of Hiking in Wicklow
- My Emerald Isle: Why Ireland is the Epitome of Home
- Life in Boulder Colorado: A Quick Guide to Boulderites’ Lifestyle, Culture, and Values
- The Spirit of Ireland: A Brief History of Irish Whiskey
- Comparison of Firearm Purchase Procedures in California vs Texas
- First impressions on Austin, Texas and its Tech Scene
- Buying a Gun in California – Not as Easy as it Sounds
- Biometric Hype: A Risky Proposition for Fingerprint and Iris Scanners
- Temple Bar: A Great Place to Live, for the Deaf Insomniacs
- Zero Trust and The Mutating Threat Landscape
- CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
- Mentors: The Priceless Few and Lessons Learned
- Selected by Hackin9 and eForensics Magazines as a Contributing Cybersecurity Expert
- Notes from the Cloud Security Alliance (CSA) Congress EMEA 2015
- Analyzing the Power Consumption of Mobile Antivirus Software on Android Devices
- Poorly Configured Proxies Leaking Information through “X-Forwarded” and “Via” HTTP Request Headers
- CyberSecurity: A Case Study of the Need for Change
- Cyberconfusion: Cyber Security, Cyber-Security or Cybersecurity?
- CyberSecurity: Origins of the Advanced Persistent Threat (APT)
- A Newcomer’s Take on Dublin Town — First Impressions
- Crypto Wars and Messaging: How Secure are Skype and WhatsApp?
- Reduced Cognitive Performance: Open-Plan Offices, Noise and Collaboration
- First Impressions on Working with Huawei’s European Research Center (ERC)
- Lessons I’ve Learnt from various Relationships
- Money and Friends Don’t Always Mix
- X-Pyr 2014: My Annotated Version — An Assistant’s View of the Competition
- Malta Airport Gives Schengen a Slap in the Face
- Officially Selected for the X-Pyr 2014 Competition to Cross the Pyrenees by Paraglider
- A Scuba Diver Never Loses His Stripes
- I’ve Reached Middle Age, or so they say, welcome to the Fabulous Forty (40)
- Dubai Residency Visa: Medical & Blood Tests are a Waste of Time
- Pay-to-Volunteers: A Sad State of Affairs in Africa
- Malaria: Arguably the only African natural resource unwanted by the rest of the world
- Still No Conclusive Evidence Suggesting Syrian Government Used Chemical Weapons
- Will it take one million casualties in Syria before the West gets involved?
- Taking Advantage of Idiosyncrasies and Body Language during Business Meetings and Difficult Situations
- Dubai Holds Great Earning Potential for Anglophone East-Africans
- Absence Makes The Heart Grow Fonder — Does it Really?
- Five Thousand Eight Hundred and Sixty-Two Kilometres from Home
- Avoiding Chronic Short-term Memory Loss on Large Projects
- Invited to Talk about Achieving Enjoyment at Work
- Shove your Hello Tomorrow and give me my Quiet Today
- Professional Certifications: Why get certified in the first place?
- Critique of Media Coverage on BlackBerry’s Share Price Free-fall
Great article Dr. Shem. as you suggest, the security mindset should shift from incident basis to a continual basis with the assumption of continuous compromise. this will lead to more adaptive and hopefully less costly defenses