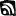CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
February 11, 2016 Shem Radzikowski No Comments

Cybersecurity attacks will continue to increase in both frequency and sophistication over time — mostly due to the blasé attitudes within the industry about what should be done. While APT tactics, techniques and procedures (TTPs) continue to be refined on a global scale, the targeted organizations either bury their heads in the sand pretending that there is nothing that can be done, or throw their arms up into the air with frustration and despair.
This is the third of a series of articles on CyberSecurity and Advanced Persistent Threats (APTs). Read Part 1 and Part 2.
Frustration and Despair
Those who are frustrated and desperate have at least tried something but perhaps failed — usually as a result of the ever-growing complexity of security offerings. One must wonder why, given so much investment into cybersecurity, it still takes a PhD to deploy and configure enterprise-grade security solutions? And even then a teenager armed with a few scripts could still bring an enterprise to its knees.
It’s true, the security ecosystem is growing in complexity and is beginning to fragment into specialized domains. A lot more diligence, effort and research is required to stay abreast of the latest threats and developments. These days, deploying anti-malware and enabling firewalls across an organization doesn’t make you a security professional. This barely scratches the surface and is completely useless in a world where APTs and Government-sponsored 300+ Gpbs DDoS attacks are just a smokescreen for the real hack data exfiltration.[1]
Expanded Look at APT Lifecycle
Earlier in the series I gave some background information on the work done by ISACA and McAfee in outlining the APT Lifecycle. These aren’t the only examples of APT life cycles, but they all seem to draw similar conclusions. The important fact to note is that in addition to the APT threats we have heard about, there is a growing number of new players who have adopted APT methodologies simply because they have proved to be successful.
This new breed of APT-like attacker is being defined as:
“One who specifically targets a person or enterprise for attack to achieve a specific purpose.
— McAfee (Intel Security)
The expanded descriptions below go into a bit more detail and form a fairly accurate overview of the life cycle being employed by sophisticated attackers.[2] APTs are committed to infiltrating their target systems, irrespective of how long it takes to achieve that goal.
- Conduct background research. APTs conduct detailed research on their targets to identify very specific avenues of attack. These scenarios represent the kind of detailed research the APT do to maximize the chances that their target will act as desired.
- Execute initial attack. Typically, the initial attack targets one or more specific individuals through some form of social engineering: embedding a link to malicious content into an email message, an instant message, a social media posting or another attack vector, and enticing the target to act by opening an attachment or clicking on a link to infect one or more devices with malicious software.
- Establish foothold. Once a user acts, the APT establish an initial foothold into the target environment using some version of customized malicious software. In almost every case, that custom software does not trigger any antivirus alert, but it does beacon to the APT to inform them of the successful attack. The initial infection tool, sometimes called first-stage malware, may have very little malicious functionality, but it generally is able to beacon home and download additional functionality, sometimes called second-stage malware.
- Enable persistence. One of the primary objectives of the APT is to establish persistent command and control over compromised computers in the target environment, meaning control and access that will survive a reboot of the targeted device and provide the APT with regular connectivity to the target environment. In most cases, this persistence is established simply by installing new services (including the attacker’s command-and-control software) on the target computer that automatically start when the computer boots.
- Conduct enterprise reconnaissance. After establishing persistent access to the target environment, the APT generally conduct enterprise reconnaissance in an effort to find the computers, servers or storage areas holding the information they have been instructed to steal. In most cases, they conduct the reconnaissance using the tools available to them on the compromised computers. In some cases, they upload scanning tools to search for specific types of systems (e.g., identity and access management, authentication, virtual private network (VPN), database or email servers).
- Move laterally to new systems. Part of enterprise reconnaissance necessarily includes moving laterally to new systems to explore their contents and understand to what new parts of the enterprise they might gain access from the new systems. They also directly install their command-and-control software on new systems to expand their persistent access to the environment.
- Escalate privileges. As the attackers conduct reconnaissance and move around the network using the compromised credentials of their first few targets, they inevitably seek to escalate from local user to local administrator to higher levels of privilege in the environment so that they are not constrained to any specific part of the environment. In enterprises where access to information is tightly controlled, compromising all the credentials in the environment allows the attackers to masquerade as anyone in the environment and access any resource they desire.
- Gather and encrypt data of interest. Having found the data of interest to them, the APT generally gather the data into an archive and then compress and encrypt the archive. This enables them to hide the contents of the archive from technologies that include deep packet inspection capabilities and from data loss prevention (DLP) at the enterprise boundary.
- Exfiltrate data from victim systems. The ultimate objective of an APT attack is to steal something of value. The APT may use traditional means of transferring files, such as file transfer protocol (FTP) applications or even HTTP Post if the enterprise allows outbound communication. They might also use custom data transfer technologies operating via covert channels.
nonstandard ports if FTP is not allowed. - Maintain persistent presence. Lastly, the APTs seek to attain what they have been tasked by their controllers to do: maintain access to the target environment. It is not uncommon for the APT to sit undetected in an enterprise network for lengthy periods of time, waiting to complete their directive.
What Are Othes Doing?
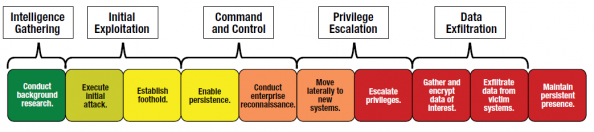
APTs are well-skilled in adapting to an ever-changing environment. In many cases, the target organization may be aware of a breach, but not know where or what to look for because the attacker is laying dormant. But even in such extreme cases of infiltration, organizations can still respond and defend themselves in a variety of ways. Figure 2 summarizes some common approaches to improving security.
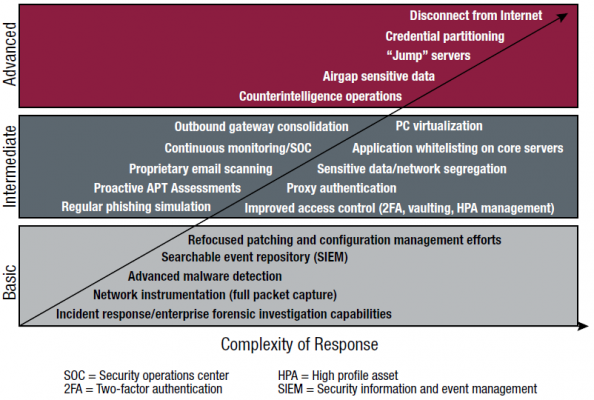
Figure 2: Complexity of Countermeasures. Src: Intel Security
It’s unlikely that every organization will implement the Advanced mitigations. Some of these mitigations are rather drastic, like disconnecting from the internet. Nevertheless, some organizations will go to any lengths to protect their security. At the very least it is advised that every organization implement the Basic mitigations and seriously look at deploying the Intermediate technologies.
Conclusion
It is clear that APT threats or APT-like threats will increase over time. As a result, organizations need to educate themselves and update their defensive postures in order to defend against these advanced threats. While there are many countermeasures that can be employed to improve security, there may be barriers, both technical and financial, why such defenses remain underemployed.
The key takeaways from this post are (1) understand how APTs operate to gain a foothold within an enterprise, (2) implement all of the Basic countermeasures mentioned in Figure 2 and deploying the Intermediate mitigations. And (3), any organization which is serious about security, should start implementing at least some of the countermeasures listed in the Advanced section.
Footnotes
- DDoS attacks are on the rise and are now starting to be seen as a smokescreen for the “real” or “secondary” attack and ultimate exfiltration of data, according to Akamai researchers. http://drshem.com/2015/11/27/notes-from-the-cloud-security-alliance-csa-congress-emea-2015/ ^
- Responding to Targeted Cyberattacks – Google Books Preview ^
Bibliography
Related
Advanced Persistent Threat, APT, Countermeasures, Cybersecurity, DDoS, Intel Security, ISACA, McAfee, Mitigation, TTP Security
Leave a Reply
Subscribe
Subscribe and receive email notifications the moment Dr.Shem publishes a new post.
Our Sponsors
Recent Posts
- My Journey with Ropes: Scaling New Heights
- Climbing Mountains in and Around Pokhara: An Adventure Beyond the Summits
- A Nomad’s Notebook: Charting My Path Across Continents
- From Pierogi to Pavlova: My Transcontinental Childhood
- Riding Through History: A Personal Journey on the Irish Rail System
- Above the Azure: Discovering the Thrills of Paragliding in Malta
- Immersed in Nature: A First-hand Experience of Hiking in Wicklow
- My Emerald Isle: Why Ireland is the Epitome of Home
- Life in Boulder Colorado: A Quick Guide to Boulderites’ Lifestyle, Culture, and Values
- The Spirit of Ireland: A Brief History of Irish Whiskey
- Comparison of Firearm Purchase Procedures in California vs Texas
- First impressions on Austin, Texas and its Tech Scene
- Buying a Gun in California – Not as Easy as it Sounds
- Biometric Hype: A Risky Proposition for Fingerprint and Iris Scanners
- Temple Bar: A Great Place to Live, for the Deaf Insomniacs
- Zero Trust and The Mutating Threat Landscape
- CyberSecurity: Expanded Look at the APT Life Cycle and Mitigation
- Mentors: The Priceless Few and Lessons Learned
- Selected by Hackin9 and eForensics Magazines as a Contributing Cybersecurity Expert
- Notes from the Cloud Security Alliance (CSA) Congress EMEA 2015
- Analyzing the Power Consumption of Mobile Antivirus Software on Android Devices
- Poorly Configured Proxies Leaking Information through “X-Forwarded” and “Via” HTTP Request Headers
- CyberSecurity: A Case Study of the Need for Change
- Cyberconfusion: Cyber Security, Cyber-Security or Cybersecurity?
- CyberSecurity: Origins of the Advanced Persistent Threat (APT)
- A Newcomer’s Take on Dublin Town — First Impressions
- Crypto Wars and Messaging: How Secure are Skype and WhatsApp?
- Reduced Cognitive Performance: Open-Plan Offices, Noise and Collaboration
- First Impressions on Working with Huawei’s European Research Center (ERC)
- Lessons I’ve Learnt from various Relationships
- Money and Friends Don’t Always Mix
- X-Pyr 2014: My Annotated Version — An Assistant’s View of the Competition
- Malta Airport Gives Schengen a Slap in the Face
- Officially Selected for the X-Pyr 2014 Competition to Cross the Pyrenees by Paraglider
- A Scuba Diver Never Loses His Stripes
- I’ve Reached Middle Age, or so they say, welcome to the Fabulous Forty (40)
- Dubai Residency Visa: Medical & Blood Tests are a Waste of Time
- Pay-to-Volunteers: A Sad State of Affairs in Africa
- Malaria: Arguably the only African natural resource unwanted by the rest of the world
- Still No Conclusive Evidence Suggesting Syrian Government Used Chemical Weapons
- Will it take one million casualties in Syria before the West gets involved?
- Taking Advantage of Idiosyncrasies and Body Language during Business Meetings and Difficult Situations
- Dubai Holds Great Earning Potential for Anglophone East-Africans
- Absence Makes The Heart Grow Fonder — Does it Really?
- Five Thousand Eight Hundred and Sixty-Two Kilometres from Home
- Avoiding Chronic Short-term Memory Loss on Large Projects
- Invited to Talk about Achieving Enjoyment at Work
- Shove your Hello Tomorrow and give me my Quiet Today
- Professional Certifications: Why get certified in the first place?
- Critique of Media Coverage on BlackBerry’s Share Price Free-fall